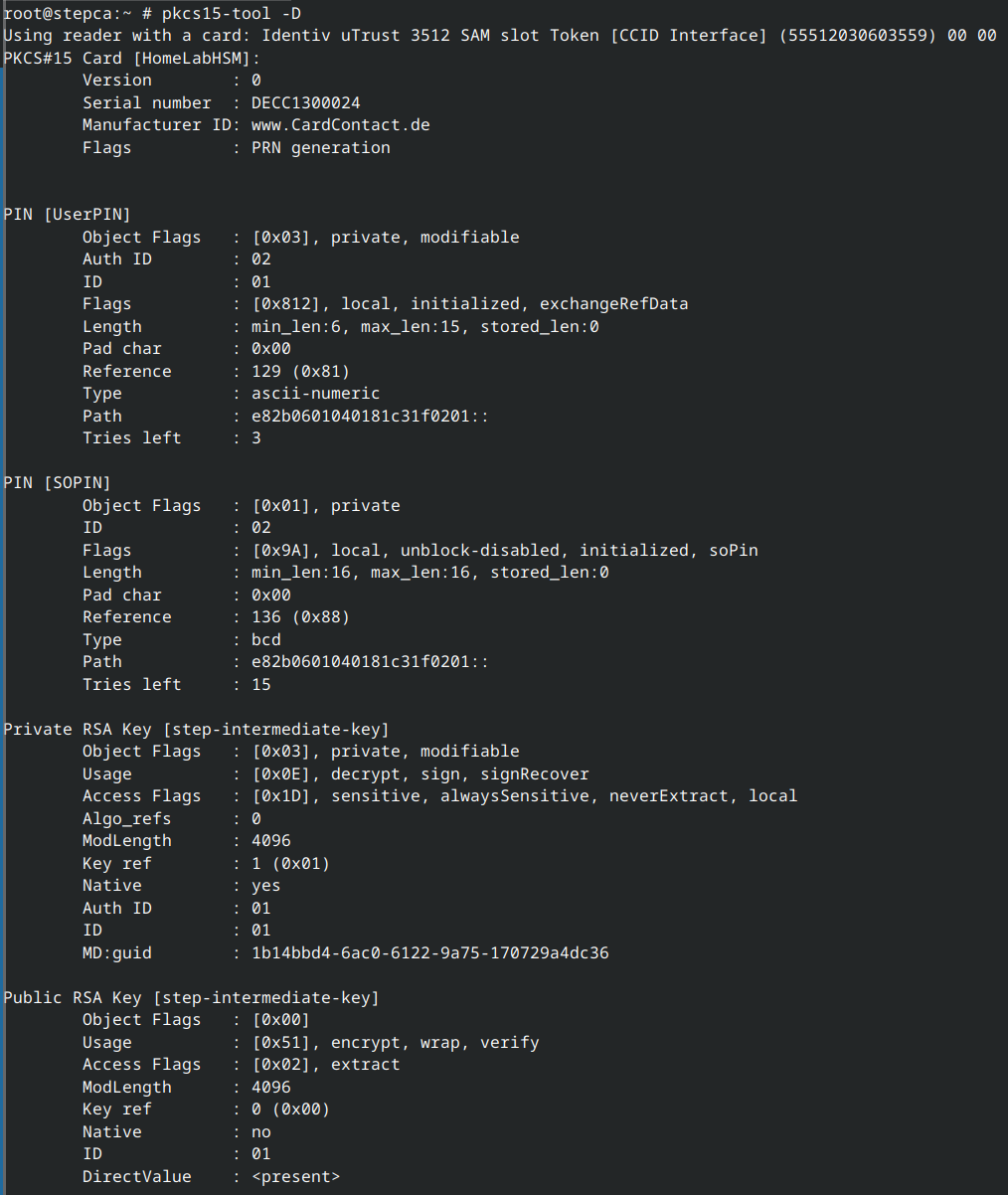
What a project. Did configure StepCA in my home-lab with a real physical HSM for the CA's private key. Using a SmartcardHSM (https://www.smartcard-hsm.com) from CardContact Systems.
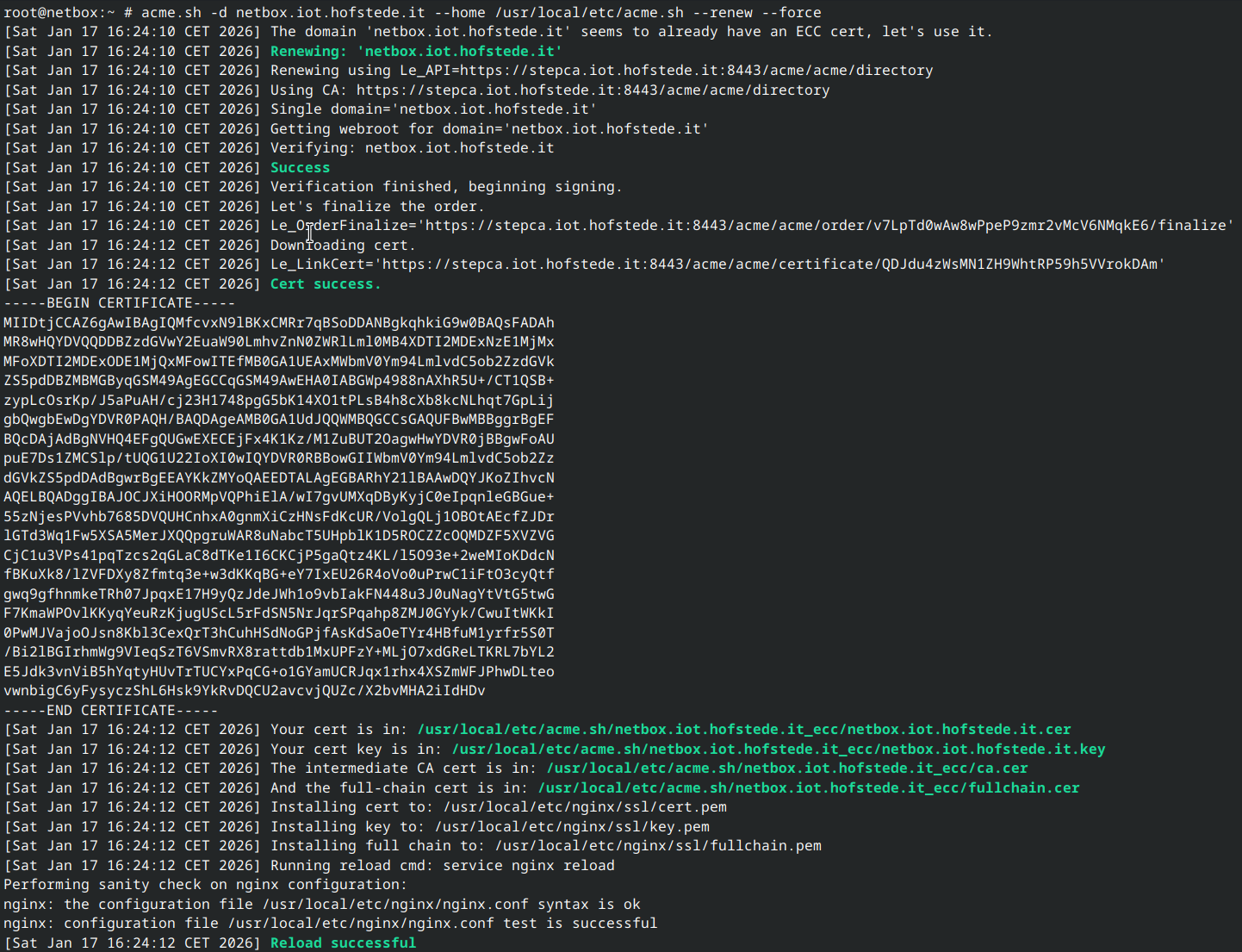
Now I have acme (automated cert provisioning) working internally as long as the HSM is plugged into my server.
All running in an isolated FreeBSD 15-RELEASE jail.
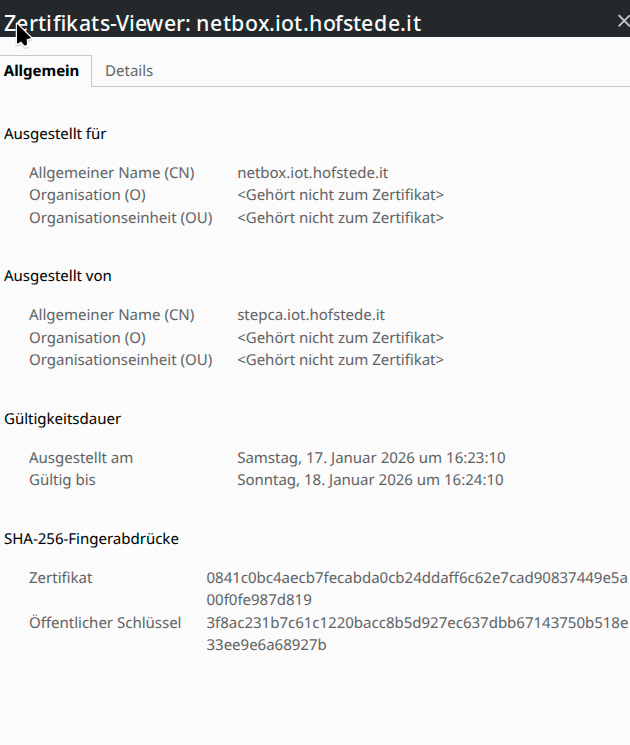
Yay! It works!
#freebsd #stepca #devops #acme #certificates #tls #smartcard #hsm