New, from me: The Kimwolf Botnet is Lurking in Corporate, Govt. Networks
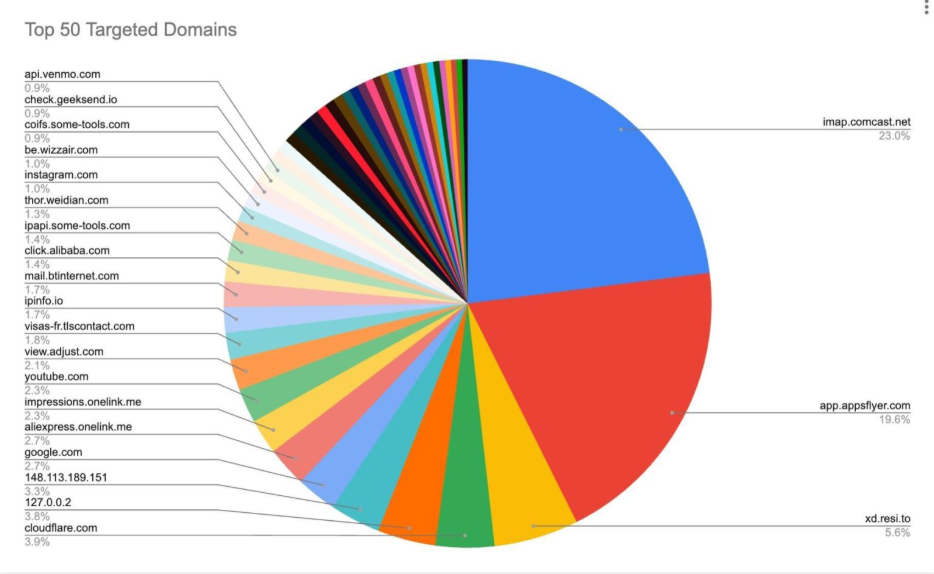
A new Internet-of-Things botnet called Kimwolf has spread to more than 2 million devices, forcing infected systems to participate in massive distributed denial-of-service (DDoS) attacks and to relay other malicious and abusive Internet traffic. Kimwolf’s ability to scan the local networks of compromised systems for other IoT devices to infect makes it a sobering threat to organizations, and new research reveals Kimwolf is surprisingly prevalent in government and corporate networks.
https://krebsonsecurity.com/2026/01/kimwolf-botnet-lurking-in-corporate-govt-networks/