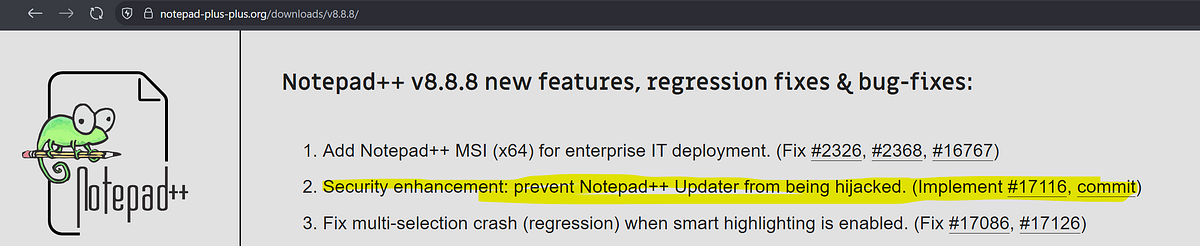
Notepad++ versions and update mechanisms had been compromised since June until December 2025. Please update to 8.9.1 wherever you have this tool. It's unclear what malicious versions of the tool might do. I Recommend activating incident response for affected hosts.
https://notepad-plus-plus.org/news/hijacked-incident-info-update/