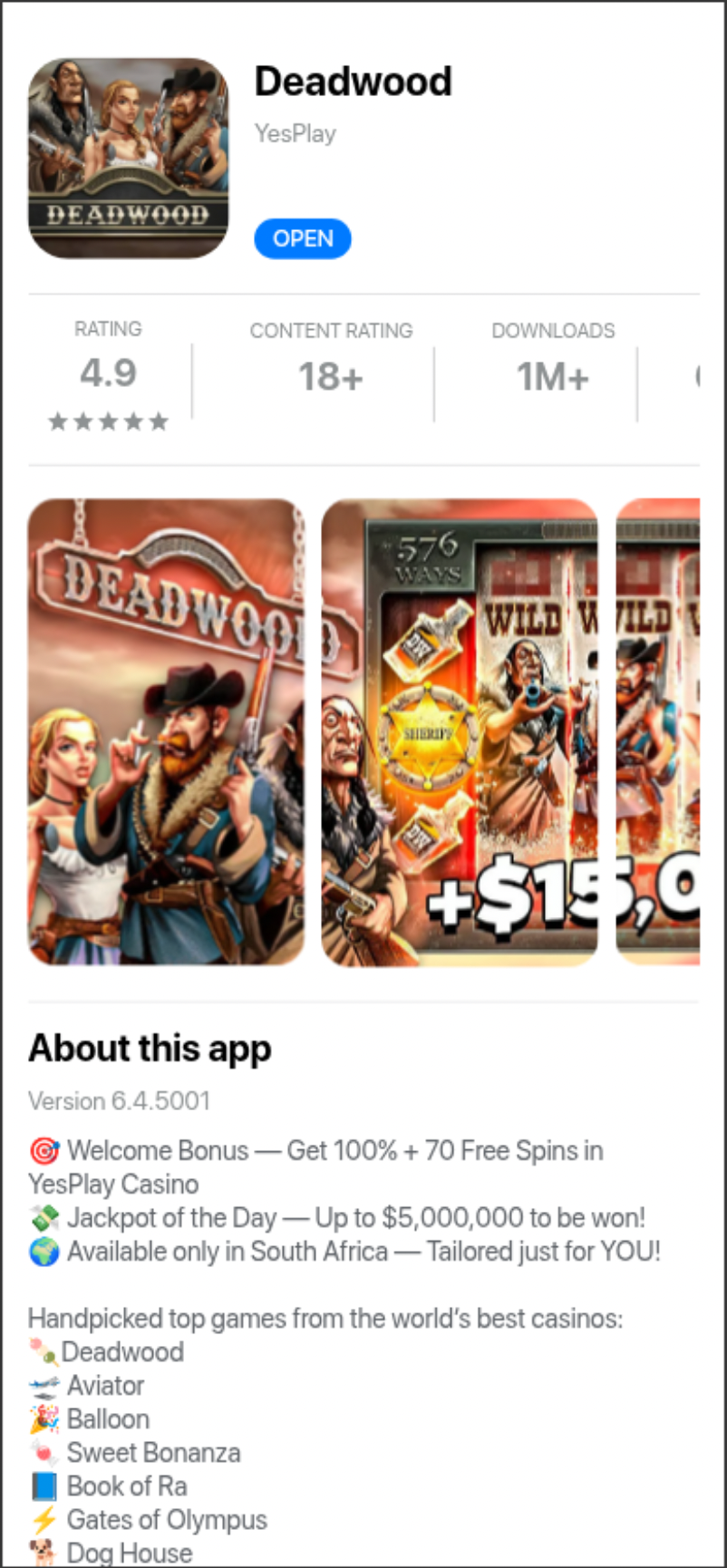
We’ve been tracking a cluster of RDGA‑generated domains involved in distributing fake app‑store landing pages. These domains are consistently registered through Namecheap and protected by Cloudflare, which the operators use to obscure origin infrastructure and rapidly cycle through fresh front‑end domains.
The sites impersonate Google Play or iTunes, based on their device’s user‑agent, presenting users with pages that look and feel legitimate. Instead of real apps, the pages deliver Progressive Web Applications (PWAs) that persist on the device and enable ongoing notification abuse.
PWAs are a chrome application which plays cross platform, windows, linux, android, iOS and gets added as an icon on the desktop ofevery device.
Once installed, the PWA triggers a redirection chain through one or more intermediary domains before sending users to online casinos, adult content, or other low‑quality destinations. Because many of these casinos operate from regions where online gambling is restricted or illegal, the operators continually replace the final‑stage domains. This use of RDGA and PWAs allows them to evade regional blocking, reputation systems, and automated detection controls by rotating infrastructure at scale and keeping their persistence to the user devices.
fwiw, most large scale gambling operations like these are not simply illegal in the regions they target... they are scams and often connected to other major crimes, including human trafficking.
play-megawin[.]site
play-icefish[.]website
play-richcasino[.]site
play-casinostaat[.]site
mountainvertex[.]shop
play-fdjfrance[.]site
play-lucky7[.]site
funterra[.]shop
hotcoins[.]site
stonefestal[.]shop
spirevanguard[.]shop
play-crowngreen[.]website
forestoutpost[.]shop
#threatintel #gambling #pwa #dns #fake #infoblox #threatresearch #malware #scam #fakeApp #googleplay #infobloxthreatintel #itunes